What is the Cyber Kill Chain?
The Cyber Kill Chain® is a framework developed by Lockheed Martin that helps organizations understand and combat cyber attacks. It breaks down the stages of a cyber attack, allowing security teams to develop specific countermeasures at each stage. By understanding these stages, organizations can better protect themselves and respond to threats effectively.
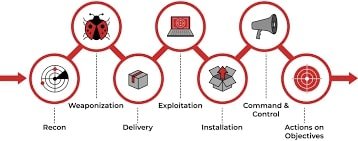
The Seven Stages of the Cyber Kill Chain
1. Reconnaissance
In this initial stage, attackers gather information about their target. This includes:
- Harvesting email addresses
- Identifying network infrastructure
- Scanning for vulnerabilities
- Social media research
- Employee information gathering
2. Weaponization
Attackers create their attack tools by:
- Developing malware
- Creating exploit payloads
- Preparing phishing templates
- Setting up command and control infrastructure
3. Delivery
The attack is transmitted to the target through various means:
- Phishing emails
- Malicious websites
- USB drives
- Supply chain compromises
4. Exploitation
The attack is triggered, exploiting vulnerabilities in:
- Operating systems
- Applications
- Human behavior
- System configurations
5. Installation
Malware or backdoors are installed to maintain access:
- Persistence mechanisms
- Backdoor creation
- Privilege escalation
- Defense evasion techniques
6. Command and Control (C2)
Attackers establish control over compromised systems:
- Remote access setup
- Communication channels
- Data exfiltration paths
- Lateral movement preparation
7. Actions on Objectives
The final stage where attackers achieve their goals:
- Data theft
- System destruction
- Ransomware deployment
- Long-term espionage
Defensive Strategies for Each Stage
Reconnaissance Defense
- Implement strong information disclosure policies
- Regular security awareness training
- Monitor digital footprint
- Control public information exposure
Weaponization Defense
- Threat intelligence monitoring
- Security research and analysis
- Vulnerability management
- Regular security assessments
Delivery Defense
- Email filtering
- Web filtering
- Network segmentation
- USB device control
Exploitation Defense
- Regular patching
- Security hardening
- Application control
- Security awareness training
Installation Defense
- Endpoint protection
- Application whitelisting
- File integrity monitoring
- Behavior analytics
Command and Control Defense
- Network monitoring
- Firewall rules
- DNS monitoring
- Traffic analysis
Actions on Objectives Defense
- Data loss prevention
- Access control
- Backup systems
- Incident response plans
Implementing the Cyber Kill Chain Framework
To effectively implement the Cyber Kill Chain framework in your organization:
- Assess your current security posture against each stage
- Identify gaps in your defenses
- Implement appropriate controls for each stage
- Develop detection and response procedures
- Regularly test and update your defenses
- Train your security team on the framework
- Maintain documentation and procedures
Conclusion
The Cyber Kill Chain framework provides a structured approach to understanding and defending against cyber attacks. By implementing defenses at each stage, organizations can create a more robust security posture and better protect their assets. Remember that cybersecurity is an ongoing process, and regular updates to your defensive strategies are essential to stay ahead of evolving threats.

